The user clicked on a link on the Apple Computer. In his eyes, everything was so calm. However, he did not know that, with the click of a bang, countless data rushed into the computer. During the five seconds of the second hand, Apple’s top programmers were destroyed by the layered defense system built by the code, and the God of cyberspace quietly changed hands. Between the electric light and the Flint, the hacker seized all the rights of the computer.
This incident really happened in the "Hacker Games" - Pwn2Own 2016. It was the hackers from the Tencent Cohen Lab that made this gorgeous attack. The heinous thing is that they also used another gesture, again causing the macOS world to crash.
It is this astounding hacker aesthetic that helped them succeed in the title of "Master of the World".
Since March of this year, the whole world has been waiting for the "masters" to reveal the secret attack method. Five months later, Cohen's hackers finally decided to restore the technical details of the attack. The stage they chose was BlackHat USA, the highest event in the hacker community.

From left to right: Gross, Flanker, Fu Yubin, and Chen Liang
The secret entrance - the amazing truth about that attack
Chen Liang, Flanker, Fu Yubin, and Gross were the main hackers who cracked macOS at the time.
The truth they told about them almost exceeded everyone's imagination: two perfect attacks, all defeating Apple's graphics rendering system. This method of attack has only appeared once in the world. And the director of the attack was still them.
This is a secret entrance.
Chen Liang told Lei Fengwang,
Remote attacks are difficult in all attacks. The preferred choice for remote attackers is the browser Safari. The two successful attacks used two sets of "Safari+ graphics rendering" vulnerabilities.
Apple also bears some responsibility for the occurrence of this kind of attack. Flanker said, "In the old Apple system, the general application is no right to call the GPU and graphics rendering system, all graphics rendering must be achieved through the "window manager"; and in the new Apple system, in order to ensure the user experience The smoothness of Apple's open applications for general applications to invoke the GPU."
This is the logical origin of all disasters.

macOS graphics rendering system working logic
Malformed dataSimply popularize it: If an app wants to draw graphics, it needs to provide some logical coordinates. These coordinates are passed to the GPU for drawing by the kernel driver, and then converted into room coordinates and appear on the display.
For Chen Liang, who has already "broken up" Safari through the loopholes, he can fake Safari's "correction" and send out various malformed data to the drawing system.
For example, a very, very long rectangle, such as a rectangle with a negative side length.
For the image rendering system, no matter how unreliable Safari's commands are, he can't resist the purpose. As a result, the poor rendering system holds a small whip, forcing the GPU to draw a rectangle with a negative side length. So the GPU side, its world collapsed, all kinds of data can not be written into the memory, the hackers mouth showing a smile.
However, this is not enough.
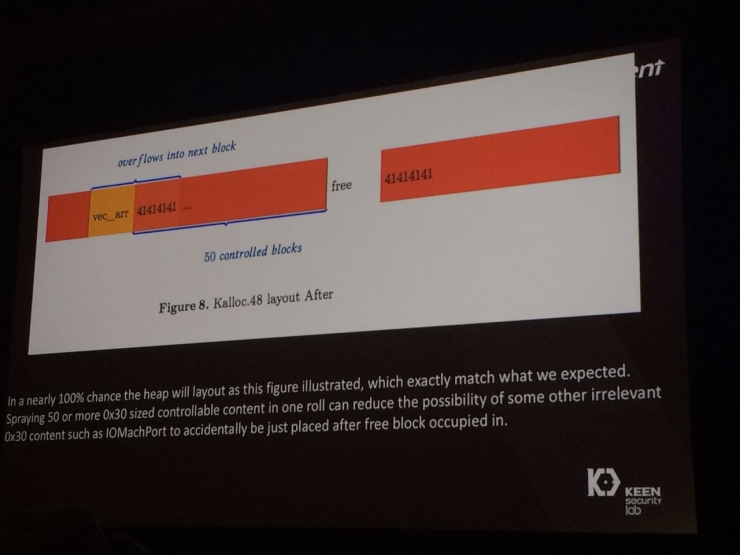
Memory overflow indication
Meticulously constructed data trapIt is obviously not the purpose of the hacker to completely crash the system. Their purpose is to precisely control this kind of crash - to make the "mourning" of the GPU form an "interesting symphony".
In order to achieve this goal, they face the "three mountains."
1. They want to make use of this tiny wound and use a scalpel to accurately arrange the code they want in memory.
2. Even if it is so difficult, Apple's code is still "closed source," and they must "guess" Apple's code logic through reverse engineering.
3, worse, the closed Apple system is far more than Windows in security protection.
In fact: Every tiny movement they make will have a large area of ​​influence.
for example,
This is like driving a forklift through the needle and completing one hundred consecutive times;
It's like playing a game with sunglasses. It doesn't cost a lot of blood to pass through.
It's like having a hundred girlfriends at the same time, and it makes them feel that they don't exist.
In short, this matter is harder than your imagination.
Live demonstration of macOS cracking process
Flanker told Lei Feng:
A relatively simple vulnerability allows hackers to write arbitrary values ​​at arbitrary addresses. This situation is very easy. However, graphics-related vulnerabilities usually rely on the GPU to perform floating-point operations. So we must satisfy its nature—floating-point numbers must correspond to very large integers, so we must arrange extremely specific data in precise memory locations.
Technically speaking, they need to find a stable memory, and then within a very short period of time, they put their carefully constructed code into it. Just like a speeding train, jump to a designated door precisely. However, God does not give much power to it most of the time.
This loophole is in a more active memory area. Once memory is used, it will fail if it receives interference. So we invented a "memory feng shui theory . " Using memory to allocate certain "first-in-first-out" features, constructing some "holes", and then trying to make our code fall into this "empty".
Flanker explained.
The above technical path is a relatively complex set of two cracking solutions. They are called "kernel-based loopholes." While another set of "user-space loopholes" is similar in theory, the utilization scheme is relatively simple.
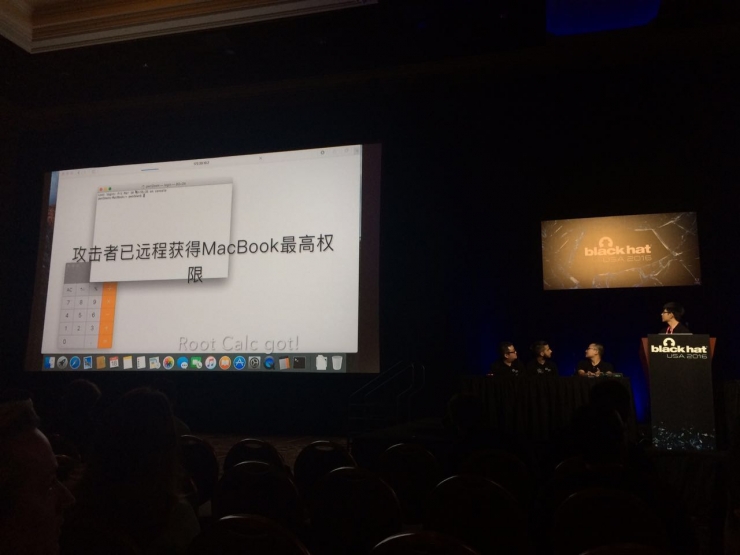
In the live demo video, the attacker obtains the highest authority of the system
Never-fallen noise VS The never-ending hacker spiritAs mentioned earlier, this kind of cracking is equivalent to "jumping on a designated car door precisely next to a speeding train." However, Flanker and Fu Yubin told Lei Fengwang (searching for "Lei Feng Net" public numbers) a cruel fact: There is a certain possibility that when you jump to the door accurately, the door is closed.
This kind of power that kills the invaders at the bottom of the Pirates’ Dream Space is still the “eternal noise†from memory. Flanker said that the "user-state vulnerability program" has a 15% to 20% chance of failure, while the "kernel-state vulnerability program" has a very low probability of failure, but it still cannot guarantee a 100% success rate.
These actual noises from cyberspace are the lowest values ​​that they have tried their best and still can't control.
In the Pwn2Own contest in March, the strict rules of the game, a team can only make up to 3 attempts in 15 minutes. That is, although the probability is small, they still have the possibility of failure.
However, this time, God, who had always been a problem for them, finally took care of them. Both programs successfully attacked each time, taking 5 seconds and 1 minute respectively.
There may be many reasons why God cares for them.
However, there is no doubt that
That is the hacking spirit of this group of Chinese hackers.

Diesel Generating Set,Genset Generator,Independent Power Supply,Office Buildings Generator
Shaoxing AnFu Energy Equipment Co.Ltd , https://www.sxanfu.com